Chicago Security Guards & Cyber Security Service";var b="+17734454300";var c="";var d="7545 S Western Ave, Chicago, IL 60620, United States";var e="";var f="";var arr=[];arr.push(decodeURIComponent("%3Cdiv%3E%3Cdiv%20style%3D%22padding%3A%208px%3B%20border%3A%202px%20solid%20grey%3B%22%3E%3Ch3%20style%3D%22margin-top%3A%204px%3Bmargin-bottom%3A0px%22%3E"));arr.push(a);arr.push(decodeURIComponent("%3C%2Fh3%3E"));arr.push(decodeURIComponent("%3Cbr%3EAddress%3A%20"));arr.push(d);arr.push(decodeURIComponent("%3Cbr%3EPhone%3A%20%3Ca%20href%3D%22tel%3A"));arr.push(b);arr.push(decodeURIComponent("%22%3E"));arr.push(b);arr.push(decodeURIComponent("%3C%2Fa%3E"));arr.push(decodeURIComponent("%3Cbr%3E%20%3C%2Fdiv%3E"));document.querySelector('#_nap_').innerHTML = arr.join('');
This is necessary due to the fact that it enables firms to maintain a competitive advantage and also maintain their product or services secure from competitors. Furthermore, it assists to ensure that new product or services are not quickly reproduced or stolen before they can be released to the market (Cyber Security Consulting). The cloud has actually changed just how we believe regarding IT, but it has actually also presented brand-new safety threats.
See This Report on Cyber Security Consulting
They need to function with their cloud service providers to make sure that ample protection controls are in location. They need to additionally think about using a cloud safety and security platform to help handle and monitor their cloud atmosphere. The web has become a staple in service procedures for most of companies throughout the globe.
By taking these actions, businesses can show their dedication to protecting client and also worker information, which can help to build and also maintain trust. The importance of cybersecurity to make certain an organization's monetary placement can not be understated. In today's interconnected world, where sensitive data is typically stored electronically, a violation in safety and security can have disastrous effects.
One more necessary aspect of cybersecurity is employee training. Employees need to be trained on just how to detect possible cyber threats and also what to do if they come across one.
What Does Cyber Security Consulting Mean?
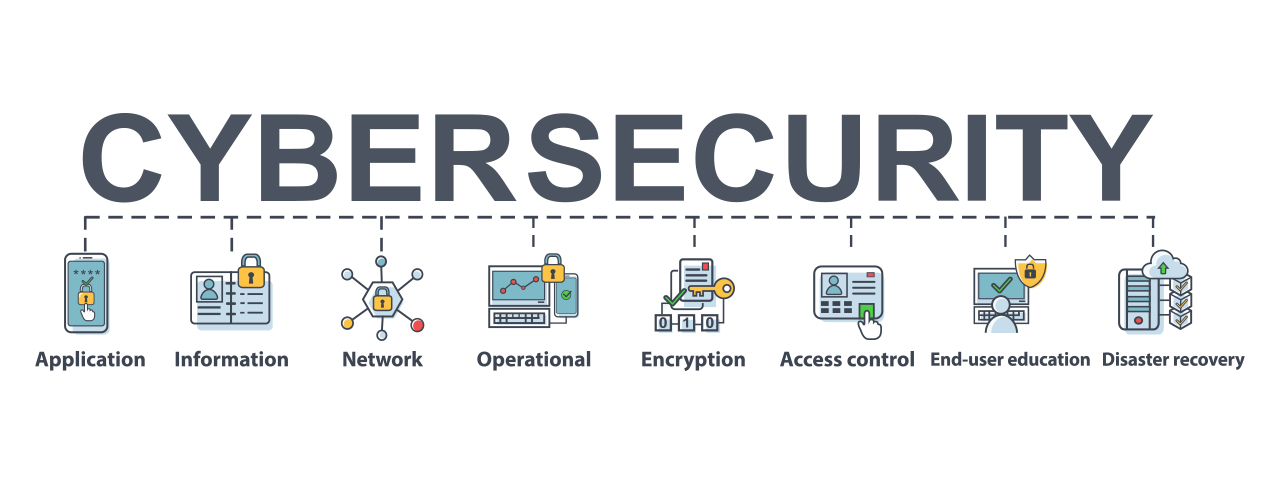
There are lots of factors why people require to protect their look at more info information. One factor is that if data is not covered, unauthorized individuals can access as well as use it.
Another factor is that if information is not secured, it can be shed or damaged, which can trigger considerable aggravation or even economic challenge. Some methods individuals can come to be much better at protecting their information are:: Passwords should be at the very least eight characters long and consist of a mix of capital and lowercase letters, numbers, as well as symbols.
And as we use it an increasing number of, we are putting more as well as more of our personal details online. This information can be made use of to swipe our identity, cash, or information. Another factor to discover the value of cybersecurity Discover More is that cyber-attacks are coming to be an increasing number of typical as well as we require to be much more mindful than ever.
A cyber assault could disable a hospital, bring down a power grid, or also start a battle. Finally, it is very important to discover regarding cybersecurity since it is an expanding sector. There are more as well as more task possibilities in cybersecurity, as well as the area will just proceed to grow.
Fascination About Cyber Security Consulting

To assist you comprehend the importance of cyber safety and security, we've assembled a blog post explaining the different components of cybercrime you may not recognize. If you're not yet fretted about cybersecurity dangers, you need to be. Cybersecurity is the state or procedure of safeguarding as well as recovering computer system systems, networks, gadgets, and also programs from any kind of cyber assault.
.jpg)
